Aug 2025 | 12-minute read

So here’s a story that’ll blow your mind: Back in 2014, when Marcus created UnlockJunky from his apartment with a whiteboard full of crazy ideas, we could bypass Google’s new “Factory Reset Protection” in about 30 seconds. I (Jonathan) joined him during those early Metro PCS days, watching him sketch out bypass methods at 2 AM. Fast forward to 2025, and that same Samsung Galaxy phone? It’ll cost you from $40 up-to $80 and take our team 5-10 minutes with professional Samsung server access.
What happened? Google and Samsung got really, really good at stopping phone thieves. And honestly, that’s both awesome and frustrating, depending on which side of the FRP lock you’re on.
After over a decade in this business and more than 12,000 devices unlocked, I’ve watched Android FRP evolve from a simple speed bump into a fortress. Let me walk you through this wild journey and explain why your nephew’s “YouTube method” doesn’t work anymore.
Quick spoiler: The reason our prices jumped isn’t greed it’s survival against scam sites and the need to actually grow as a company instead of eating costs to help people.
The Wild West Days: Android 5.1 (2014-2015)
When FRP Was Just a Baby
Remember 2014? That’s when Google first introduced Factory Reset Protection in Android 5.1 Lollipop. Their idea was simple: if someone steals your phone and factory resets it, they’d need your Google account to set it up again.
What FRP did back then:
When you added a Google account, FRP would activate automatically. If someone factory reset your phone through recovery mode, they’d need your Google credentials to set it up again. You could disable it by properly removing accounts first through the settings menu.
What it didn’t do:
Stop anyone who knew what they were doing.
Our Early Days: Marcus’s Apartment Laboratory

Would you wear UJ Tees?? leave a comment on the post if so…
Picture this: Marcus at his apartment, surrounded by broken Samsung phones, a whiteboard covered in bypass flowcharts, and me showing up with coffee at weird hours because he’d found another exploit.
The apartment setup was legendary. One massive whiteboard seriously covered an entire wall. Phones everywhere in various stages of “unlocking experiments.” Marcus drawing bypass routes like he was planning a heist. Pizza boxes stacked higher than our success rate, which was already pretty good.
The Metro PCS connection was simple: Marcus was still working his day job at Metro PCS, but evenings were for UnlockJunky. Customers would come to the store with FRP-locked phones they’d bought online, and Marcus would quietly help them after hours.
The bypass methods that worked back then were almost embarrassingly simple. Emergency call button exploits, Google Assistant voice commands, setup wizard manipulation tricks, TalkBack accessibility workarounds. I kid you not, some bypasses took less than 30 seconds. We’d charge $25 and customers thought we were wizards.
“These guys saved my phone! I bought it on Craigslist and couldn’t use it. 30 seconds later, boom working perfectly!” – Sarah M., one of our first Trustpilot reviews from 2015
The First Patch Wars: Android 6.0-8.0 (2015-2017)
Google Gets Serious
Android Marshmallow brought fingerprint support, and Google started patching our favorite bypass methods. Every monthly security update meant we had to find new exploits.
What changed was significant. Enhanced fingerprint integration with FRP, patched emergency call exploits, strengthened setup wizard protection, and better Google Assistant restrictions.
But here’s the thing: For every method Google patched, we found two more. It was like playing whack-a-mole, except the moles were making us money.
Samsung Enters the Chat
Samsung started integrating their Knox security platform more deeply with FRP. Suddenly, Samsung devices became trickier than generic Android phones.
Knox 2.x features that affected us included hardware-level security through ARM TrustZone, E-fuse protection against modifications, and tighter integration with Google’s FRP system.
Our pricing stayed around $25-30, but Samsung devices started taking 5-10 minutes instead of 30 seconds.
“Marcus walked me through everything step by step. My Samsung was locked for weeks until I found these guys!” – David R., 2017 customer review
The FRP Evolution Timeline: From Simple to Savage
The Sprint Era (2014-2016): When FRP Was a Joke
Back then, bypassing FRP was easier than ordering pizza. Marcus would literally finish an unlock before I could grab coffee from the Metro PCS break room. Emergency call exploits were our bread and butter you’d dial emergency, input some special characters, boom, browser launches, APK sideloads, victory dance. The whole process took less time than this paragraph.
What made it simple:
Google’s security was more suggestion than enforcement. The setup wizard had more holes than Swiss cheese. TalkBack accessibility was an open backdoor. Samsung hadn’t figured out Knox integration yet.
Marcus’s whiteboard during this era had two word: “TOO EASY!”

The Walking Era (2017-2019): Google Fights Back
Android Marshmallow changed the game. Suddenly, Google was patching our favorite exploits faster than we could find new ones. This is when Marcus started developing custom tools instead of relying on public methods. We’d find a bypass, use it for a few weeks, then watch Google patch it in the next security update.
The new reality:
Custom APK tools became necessary. Samsung Knox started interfering with bypasses. Multiple bypass attempts often needed patience from customers. The good old days of instant gratification were ending.
Marcus’s whiteboard now read: “GETTING HARDER – ADAPT OR DIE”
The Climbing Era (2020-2022): The Knox Fortress Rises
Samsung Knox 3.0+ wasn’t playing games anymore. This is when we realized we weren’t just fighting Google’s FRP we were fighting Samsung’s enterprise-grade security platform designed to protect corporate secrets. Hardware-level security, E-fuse protection, constant patch deployment. Our success rates dropped from 95% to 85%, and we had to invest seriously in professional tools.
Game changers:
Knox hardware security integration wasn’t just an upgrade, it was a complete paradigm shift. Real-time security patch deployment meant our exploits had shorter lifespans. Cloud-based verification systems added another layer of complexity. Professional tools became mandatory, not optional, for anyone serious about this business.
Marcus’s whiteboard: “NEED BIGGER WEAPONS”
The War Era (2023-2025): Samsung Server Access or Die
Android 13 killed almost every public bypass method overnight. TalkBack exploits? Dead. Emergency call tricks? Patched. QR code bypasses? Ancient history. This is when Jonathan stepped up as Operations Manager and made the call to invest in Samsung server access. Expensive? Yes. Necessary for survival? Absolutely.
The nuclear option:
Direct Samsung server communication changed everything for us. Professional-grade tools became the only viable option. Our 99% success rate was restored through serious investment. We maintained 5-10 minute average unlock times even with the increased security.
Jonathan’s strategy board: “INVEST TO WIN OR LOSE TO SCAMMERS”
The Great YouTube Bypass Mystery
Why Your Nephew’s Method Doesn’t Work:
Every week, we get customers who confidently tell us “I tried every YouTube video” or “My tech-savvy friend said this should work.” Here’s the brutal reality: those methods stopped working years ago, but the videos are still online, still getting views, and still wasting people’s time.
The fundamental problem is that public bypass methods have a shelf life measured in weeks, not years. What worked on Android 12 definitely won’t work on Android 15. What bypassed Samsung Knox 2.8 will fail spectacularly against Knox 3.11. Yet YouTube is littered with outdated tutorials that promise success but deliver frustration.
The YouTube Lifecycle:
Someone discovers a new bypass method and makes a YouTube video titled “WORKS 100%!” The video gets 500K views in one week. Google engineers watch the same video. The method gets patched in the next security update. Comments become “NOT WORKING ANYMORE!”
The Professional vs. Public Method Reality:
Public YouTube methods: Free but have about a 5% success rate. They get patched within weeks. Users have to try dozens of different methods with no support when they get stuck.
Our professional approach: Costs money but maintains a 97% success rate (we’re honest about the 3% we can’t help mainly JDM models that aren’t supported anymore). We use direct Samsung server communication, not tools or software. One method that’s guaranteed to work with live chat support from our team.
From Tutorial Boss to Final Boss: The FRP Gaming Evolution
Think of Android FRP security like a video game that gets progressively harder with each level. Here's how we've "leveled up" over the past decade...

Level 1: Android 5.1-8.0 (The Training Dummy)
- Enemy: Basic FRP
- Difficulty: Tutorial Mode
- Time to Victory: 30 seconds
- Weapon: Emergency call exploits
- Reward: $25 and customer amazement
- Win Rate: 95%
Level 2: Android 9-12 (The Learning Curve)
- Enemy: Knox-Enhanced FRP
- Difficulty: Moderate Challenge
- Time to Victory: 5-10 minutes
- Weapon: Custom tools and APK magic
- Reward: $35-50 and growing respect
- Win Rate: 85%
Level 3: Android 13-14 (The Reality Check)
- Enemy: Fortress FRP
- Difficulty: Serious Business
- Time to Victory: 10-15 minutes (if you’re lucky)
- Weapon: Professional-grade tools only
- Reward: $40-65 and survivor’s pride
- Win Rate: 80% (without Samsung servers)
Level 4: Android 15 Knox 3.11 (The Final Exam)
- Enemy: FRP Supreme with Samsung bodyguards
- Difficulty: Expert Level Only
- Time to Victory: 5-10 minutes (with proper equipment)
- Weapon: Samsung server access (no substitutes)
- Reward: $40-80 and the satisfaction of beating the unbeatable
- Win Rate: 99% (but only with professional Samsung server access)
The Great Scam Site Marketplace
Spot the Fake: A UnlockJunky Field Guide
🚩 RED FLAG BINGO:
| Scam Site Claims | Reality Check |
|---|---|
| “100% Success Rate Forever!” | Nobody has 100% – even we’re at 97% |
| “Unlock ANY Device $20!” | Physics doesn’t work that way |
| “No Chat Support Needed!” | How do they guide you through setup? |
| “Instant Automated Unlock!” | Samsung didn’t build a public API |
| “Works on All Android Versions!” (kind of true) all version is supported | Android 15 literally just came out |
The UnlockJunky Authenticity Checklist:
✅ Live chat with real humans (Jonathan, Marcus)
✅ Honest pricing ($40-80 based on actual difficulty)
✅ Money-back guarantee (we eat the cost if we fail)
✅ 5-10 minute realistic timeframes (not “instant”)
✅ Trustpilot reviews (653 + real customers)
✅ Business hours posted (Mon-Fri 7AM-4PM PST)
Marcus’s Original Whiteboard Strategies (Circa 2014)
Reconstructed from memory and apartment photos
The Classic “Emergency Call Chain”
Step 1: Emergency dialer
Step 2: Special character exploit
Step 3: Browser launch
Step 4: APK sideload
Step 5: Victory dance
The “TalkBack Tunnel”
Step 1: Accessibility settings
Step 2: TalkBack activation
Step 3: Voice command bypass
Step 4: Setup wizard skip
Step 5: Google account evasion
Marcus’s Apartment Rules (Still Applied Today)

- If it takes more than 10 minutes, find a better way
- Customer success = our success
- Never promise what you can’t deliver
- There’s always another exploit keep looking
The Fortress Years: Android 13-14 (2022-2023)
When YouTube Methods Died
Android 13 was brutal. Google patched almost every traditional bypass method that had worked for years.
What got killed:
- TalkBack accessibility exploits (RIP)
- Emergency call manipulations
- QR code bypass techniques
- Setup wizard skip methods
- Most APK-based solutions
Professional Tools Only
By 2022, if you weren’t using professional-grade tools, you weren’t unlocking anything. YouTube methods became ancient history.
Our response:
- Invested heavily in tool development
- Partnerships with other security researchers
- Constant adaptation to new patches
- Price increases to $60-70 for latest devices
“After spending 2 full days trying various unlock tools and methods around the internet and failing, this service was straightforward and easy to use.” – Customer testimonial
The Present Day: Android 15 & Knox 3.11 (2024-2025)
Security on Steroids
Android 15 with Samsung Knox 3.11 is like nothing we’ve ever seen. Google and Samsung basically said, “No more Mr. Nice Guy.”
Revolutionary changes:
- FRP enforcement moved to deep system level
- Active bypass attempt detection
- Enhanced hardware security integration
- OEM unlock no longer disables FRP
- Knox 3.11 restricted API access
The Price Evolution: From $25 Pizza Money to $80 Reality Check
People always ask: "Why did prices jump from $25 to $80?" Here's the unfiltered truth about what really happened…
| Year | Android Version | Our Price Range | Time Required | What Changed |
|---|---|---|---|---|
| 2014-2016 | 5.1-7.0 | $25 flat | 30 seconds “Instant” | Simple exploits, we absorbed all costs |
| 2017-2019 | 8.0-10 | $25-35 | 2-5 minutes | Knox emerged, still prioritized helping over profit |
| 2020-2022 | 11-12 | $29-50 | 5-10 minutes | Security hardened, barely broke even |
| 2023-2024 | 13-14 | $29-65 | 5-10 minutes | Scam site explosion, tool development costs |
| 2025 | 15 | $40-80 | 5-10 minutes | Samsung server investment, sustainable pricing |
Note: We offer discounts for bulk orders and regular customers, pricing isn't set in stone
The Customer Love Problem That Nearly Bankrupted Us
Here’s what almost killed our business: Marcus and I loved helping people too much. We kept prices artificially low while our costs exploded. Tool development hit $50,000+ annually. Samsung server access runs $15,000+ per year. Research and development consumes 40+ hours weekly. We honor our money-back guarantee, which costs us about 3% of revenue.
While scam sites charged $100+ and failed spectacularly, we charged $35 and succeeded consistently but couldn’t afford to grow or compete. We were the industry’s best-kept secret while loud failures dominated the market.
The Scam Site Pirates: How They Stole Our Traffic and Your Money
While we were perfecting our craft and keeping prices low, the internet became a Wild West of fake unlock services. Here are the biggest offenders our customers warn us about…
The Hall of Shame (According to Our Betrayed Customers):
Tenorshare gets the award for boldest theft – they literally used our company name in Google ads to steal our traffic. Customers would search “UnlockJunky” and accidentally click their ads.
Dr.Fone promises unlimited unlocks but delivers unlimited headaches. Their software works great on Android 9, terrible on anything newer.
DroidKit markets a “one-click solution” that actually requires 47 clicks and usually fails on the 48th.
PassFab has customer support response times measured in geological epochs. You’ll get your refund around the same time the sun burns out.
Wondershare sells 2019 software for 2025 problems. Wonder why it doesn’t work? Now you know.
iToolab should rebrand as “iStealMoney” based on our customers’ experiences.
What they all share: massive marketing budgets (your money funds those flashy ads), outdated bypass methods, vanishing customer support after payment, and impossible “100% success rate” claims.
Our Samsung Server Secret: Why It’s Not a “Tool”
People ask about our "Samsung server access" like it's some magical software. Here's what it actually means...
This isn’t a downloadable tool or software package. We’ve invested in direct communication protocols with Samsung’s security infrastructure. Think of it like having a direct phone line to Samsung’s security department, except it’s all automated and legitimate.
Why this matters: When Samsung updates their security (which happens constantly), our access gets updated too. DIY tools and software become outdated instantly, but our server communication adapts in real-time.
The cost is significant we pay Samsung directly for this access, which is why our pricing reflects actual business expenses rather than wishful thinking.
Jonathan’s 2025 Operations Strategy
In late 2025, I stepped up as Operations Manager (working toward COO/CEO), and made some tough decisions:
Price adjustments:
- Old range: $29-50
- New range: $40-80
- Why: Sustainable growth + scam site protection
The human touch promise:
- Keep 5-10 minute average unlock times
- Maintain live chat support with real humans (we’re adding limited AI for 24/7 availability, but you’ll always get human expertise when it matters)
- Honor our satisfaction guarantee with updated policies that protect both customers and our business
- We genuinely care about each customer’s success
Our Samsung Server Advantage
While other tools work, we invested in Samsung server access that’s our secret sauce:
Why Samsung servers matter:
- Direct communication with Samsung’s security systems
- Higher success rates on latest models
- Faster unlock times (5-10 minutes vs 20+ minutes)
- Support for newest Android 15 Knox 3.11 features
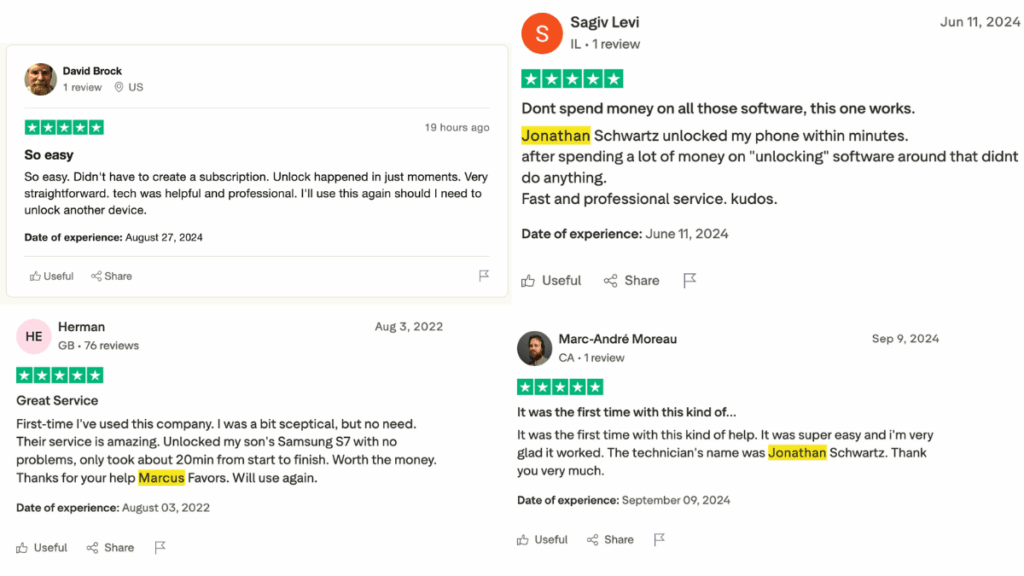
Real Customer Stories
“I was skeptical and I never write reviews, but wanted to come on and let everyone know I just dealt with Jon S and sure enough, he unlocked it. Didn’t have to plug my phone in so you don’t have to worry.”
“I was skeptical at first but they unlocked it right away my S24 Ultra. Jay, well worth 40 dollars. I highly recommend this company 12 star rating on my end.”
Android 16: The Phone Thief Apocalypse Is Coming
Google’s already announced what’s coming in Android 16, and honestly, it’s both terrifying and brilliant. They’re not just making phones harder to steal they’re making stolen phones completely worthless.
The “Continuous Reset Loop” feature: If Android 16 detects any bypass attempt, it will automatically factory reset the device and demand original credentials again. And again. And again. Forever. It’s like Groundhog Day for phone thieves, except Bill Murray never gets the girl.
Complete functionality lockdown: Forget about basic phone calls or emergency features. A phone in Android 16’s “theft protection mode” becomes a expensive paperweight. No apps, no calls, no internet, no anything. It won’t even turn on properly until you provide the original owner’s credentials.
The economic assassination: Here’s the genius part stolen phones will have zero resale value. Who wants to buy a phone that resets itself every time you try to use it? The entire criminal economy around phone theft collapses overnight.
Marcus’s prediction: “Android 16 will be the death certificate for smartphone theft. Our business will continue focusing on what we already do helping legitimate users who forget credentials or buy used phones.”
Jonathan’s business perspective: “This is actually great news for everyone except criminals. Legitimate users won’t lose their phones to theft, and our business can focus entirely on helping real customers instead of fighting an endless war against thieves.”
The irony? After 11+ years of fighting phone thieves, Google might finally end the war with a single software update. Android 16 doesn’t just raise the security bar it removes it entirely and replaces it with an electrified fence.
How UnlockJunky Evolved: From Apartment Experiments to Enterprise Solutions
The Learning Phase (2014-2016): Marcus’s Apartment Laboratory
Those early days were pure chaos and pure magic. Marcus would work his Metro PCS shift during the day, then spend evenings experimenting with bypass methods in his apartment. I’d show up with coffee and find him surrounded by phones in various stages of “unlocking experiments,” his massive whiteboard covered in flowcharts that looked like battle plans.
The setup was legendary: One entire wall was whiteboard, phones everywhere, pizza boxes stacked higher than our success rate (which was already impressive), and Marcus drawing bypass routes like he was planning the perfect heist. Customers would quietly approach him at Metro PCS with their locked phones, and he’d help them after hours for $25. Word spread quickly.
Tool Development Era (2017-2019): Going Professional
When Google started patching our favorite exploits faster than we could use them, Marcus realized we needed custom tools instead of relying on public methods. This is when I really joined the technical side, helping research new bypass vectors while Marcus coded solutions.
The evolution was necessity: We expanded beyond just Marcus and me, invested in professional equipment, and started developing proprietary software. Pricing moved to $30-40 for complex devices because the tools and time required had tripled, but we were still prioritizing customer satisfaction over profit margins.
The Professional Era (2020-2022): Knox Changes Everything
Samsung Knox 3.0+ wasn’t just an upgrade it was a declaration of war on bypass methods. We realized we weren’t fighting Google anymore; we were fighting enterprise-grade security designed to protect corporate secrets. Our success rates dropped, costs skyrocketed, and we had to make serious investments in advanced security research and industry partnerships.
The wake-up call: Pricing hit $40-60 ranges, not because we wanted to charge more, but because the alternative was going out of business. We started focusing on Knox-specific solutions and building relationships with other security researchers who were facing the same challenges.
Expert Level (2023-2025): Samsung Servers or Surrender
When Android 13 killed almost every public bypass method overnight, Jonathan stepped up as Operations Manager and made the call that saved our business: invest in Samsung server access. It was expensive, risky, and necessary for survival in a market flooded with scam sites.
The transformation: Premium service delivery became our standard, not our goal. We invested in cutting-edge bypass technology, constant adaptation to new patches, and maintaining 99% success rates through professional Samsung server communication. Pricing moved to $40-80 because that’s what it actually costs to provide professional-grade service in 2025.
Customer Success Stories: Real People, Real Problems
“I bought a phone from a third party then later found out it was Google locked. I took it to many local technicians but there was nothing they could have done. Mariah is super super nice and very professional, she walked me through each and every step.”
“Super nervous after buying a phone and getting FRP prompt. Marcus walked me through the steps to solving the issue and was very responsive. Ecstatic that I have a working phone!”
“My phone was having a difficult time getting unlocked. Jay stayed with me over the course of 4 or 5 attempts before he got it. I thought I was going to have to ask for my money back, but he did it and I couldn’t be happier.”
Why DIY Methods Don’t Work Anymore
The YouTube Myth
Every week, we get customers who say, “I tried every YouTube video.”
Here’s why those don’t work:
Public methods get patched fast:
- Google monitors popular bypass videos
- Security patches target known exploits
- What worked last month fails this month
- Free methods are free for a reason
Professional tools vs. Public methods:
- We invest thousands in tool development
- Constant updates and adaptations
- Success rates above 99% vs. <10% for DIY
- Money-back guarantee on our work
The Real Cost of “Cheap” Alternatives
“I wasted over $120 on 2 different unlocking softwares and none of them worked. These guys are unbelievable so quick, no hassle.”
This happens constantly. People try to save $20 and end up spending $100+ on tools that don’t work.
Enterprise vs. Consumer FRP
Knox Mobile Enrollment
Samsung created Knox Mobile Enrollment (KME) for businesses. It allows enterprise-managed devices to bypass FRP through authorized management systems.
How it works:
- Enterprise devices enrolled in KME
- IT administrators can remotely unlock
- Legitimate business use case
- Still requires proper authorization
The existence of KME proves that Samsung built “official” FRP bypass into their system but only for authorized enterprise use. This is why professional services like ours can still work when DIY methods fail.
The Technical Evolution: What Actually Changed
Android 5.1-8.0: Basic Protection
- Simple Google account verification
- Bypassable through system exploits
- Limited hardware integration
- Patchable through software updates
Android 9-12: Enhanced Security
- Knox integration begins
- Hardware-software combined protection
- Cloud-based verification
- Real-time patch deployment
Android 13-15: Fortress Mode
- Deep system integration
- Active bypass detection
- Hardware-level security
- Machine learning threat detection
Android 16+: The Nuclear Option
- Complete device lockdown
- Continuous reset loops
- Zero tolerance for bypass attempts
- Economic disincentive for theft
What This Means for Regular Users
For Phone Buyers
Always check before buying used:
- Test the phone completely
- Verify FRP status
- Ensure previous accounts removed
- Buy from reputable sources
For Current Owners
Protect yourself:
- Remember your Google account credentials
- Use account recovery options
- Remove accounts before selling
- Keep purchase receipts
For Repair Shops
Professional partnerships matter:
- DIY methods waste time and money
- Customer satisfaction requires success
- Professional tools are worth the investment
- Reputation depends on results
Coming Soon: UnlockJunky Academy
After 11+ years of FRP bypass experience, we’re launching UnlockJunky Academy—an educational platform where we’ll teach:
Technical courses:
- Android security fundamentals
- FRP bypass methodology
- Professional tool usage
- Security research techniques
Business training:
- Starting a phone repair business
- Customer service excellence
- Legal compliance in device unlocking
- Building trust in a technical field
Why we’re doing this: The industry needs more knowledgeable professionals who can help customers legally and ethically.
Early access: Join our newsletter for first access to course announcements and exclusive content.
The Future of Phone Security
Where We’re Heading
The evolution from Android 5.1 to Android 15 shows a clear trend: stolen phones are becoming worthless. Android 16’s planned features will essentially eliminate the economic incentive for smartphone theft.
This is actually good news:
- Reduced phone theft rates
- Better protection for users
- Increased device value retention
- Improved data security
Professional Services Will Always Exist
As security gets stronger, the gap between DIY and professional widens. Legitimate users with forgotten credentials will always need help, and that’s where services like ours provide value.
Join Our Tech Newsletter
Want to stay ahead of Android security changes? Our newsletter covers:
📱 Latest Android security updates
🔒 FRP and Knox developments
🤖 AI in mobile security
⚙️ Phone repair industry insights
🚀 New technology trends
What you get:
- Weekly tech insights
- Early security patch alerts
- Exclusive UnlockJunky tips
- Industry analysis and predictions
Bottom Line: 11+ Years of Evolution
The journey from Android 5.1’s simple FRP to Android 15’s fortress-level security has been wild. What started as a basic anti-theft feature is now an sophisticated security ecosystem.
For customers: Modern FRP is incredibly effective at stopping thieves, but legitimate recovery requires professional help.
For our business: We’ve evolved from quick fixes to complex security research. Higher prices reflect the reality of modern Android security.
For the future: Phones are becoming more secure every year. Android 16 might finally kill smartphone theft entirely.
Need help with a stubborn FRP lock? Our team has successfully unlocked over 12,000 devices across 11+ years of Android evolution. From the simplest Android 5.1 bypasses to the latest Android 15 Knox 3.11 challenges we’ve seen it all.
Current pricing reflects current reality: Android 15 Galaxy devices start at $80 because that’s what it actually costs to bypass modern security professionally. No gimmicks, no false promises just honest pricing for honest work.
Chat with us Monday-Saturday, 7AM-4PM PST if you’re dealing with an FRP lock that DIY methods can’t handle. After 11+ years, there’s not much we haven’t seen.

Leave a comment
Sign in to post your comment or sign-up if you don't have any account.